Send Windows logs to Graylog with NXLog
Table of Contents
I. Introduction
In this tutorial, we'll learn how to install and configure NXLog on Windows Server, so as to send Windows logs to a Graylog server. In this way, logs stored in the Event Viewer of several Windows machines can be stored and indexed in Graylog.
To follow this tutorial, you need a Graylog server and a machine running Windows Server (or Windows). As a reminder, in a previous article, we learned how to install Graylog on Debian :
By default, Windows is unable to send its logs to a Graylog server (or equivalent), as the log transfer functions are very limited. To solve this problem, we're going to use the community version of the NXLog agent. It will capture logs on the Windows machine and route them to the Graylog server.
II. Creating an NXLog input in Graylog
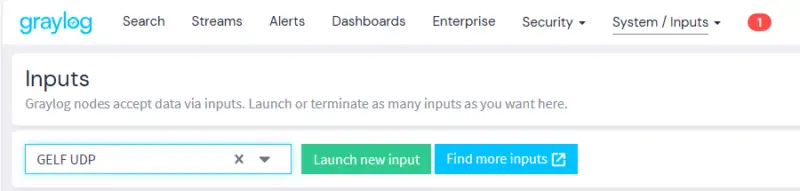
The first step is to create a new "Input" in the Graylog configuration, as this is how data is received. From the Graylog web interface, click on the "System" menu, then on "Inputs". Then select"GELF UDP" from the list, and click on "Launch new input".
Note : GELF (Graylog Extended Log Format) corresponds to the Graylog log format and will be transmitted via the UDP protocol.
A window appears on the screen... You need to configure this new Input. You can use one Input for each type of machine: one Input can be used by several Windows machines. Name this Input, for example "Graylog_UDP_NXLogs_Windows", and specify "0.0.0.0" as "Bind address" so that it can be accessed on all interfaces of the Graylog host (adjust if you have several interfaces). We can see that the connection will be made on port 12201.
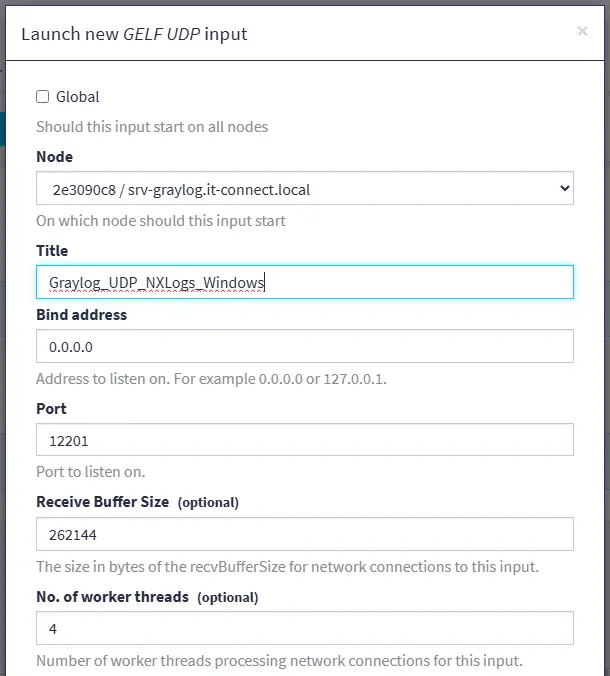
Confirm. You'll see an output similar to the one below.
Now that Graylog's configuration is complete, we'll move on to the Windows host.
III. Installing and configuring NXLog on Windows
A. Installing NXLog on Windows Server
Connect to the Windows machine, running Windows Server 2025 and named "SRV-ADDS-01" in my case, and start by downloading the NXLog agent. We'll take the community version, as it's free. It doesn't have all the features of the Enterprise version, but it's already very complete.
Click on the following link:
Then select "Windows", check the "Windowz x86-64" box and launch the download.
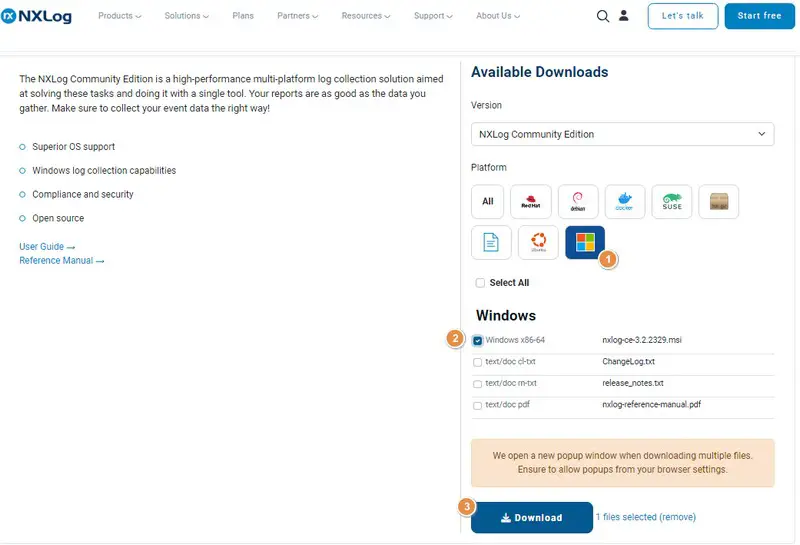
On your Windows machine, run the installation via the "nxlog-ce-3.2.2329.msi" package. Follow the wizard and complete the installation... Configuration will follow. Since this is an MSI package, we can easily deploy it on a set of machines to automate installation.

B. Configuring NXLog for Graylog
Now that NXLog is installed on the machine, we can edit its configuration file located at the following location:
C:\Program Files\nxlog\conf\nxlog.confIn addition to the configuration already present in the "nxlog.conf" file, you must add these lines at the end:
# Retrieve event viewer logs
<Input in>
Module im_msvistalog
</Input>
# Declare Graylog server (according to input)
<Extension gelf>
Module xm_gelf
</Extension>
<Output graylog_udp>
Module om_udp
Host 192.168.10.220
Port 12201
OutputType GELF_UDP
</Output>
# Routing flows in to out
<Route 1>
Path in => graylog_udp
</Route>A few explanations are in order to help you understand:
- im_msvistalog: this is the module declared as Input for retrieving logs from the Windows Event Viewer, compatible with Windows Server 2008 and Windows Vista. It is still compatible with the latest versions, i.e. Windows 11 and Windows Server 2025. For versions prior to Windows Server 2008, use the "im_mseventlog" module.
- om_udp: this is the module declared as output(Output graylog_udp). In this block, you must modify the IP address, as it corresponds to the Graylog server(192.168.10.220), and optionally the port. We use the "GELF_UDP" output type to remain consistent with the Input declared in Graylog.
- Route 1: this is a "routing" rule in NXLog to take what corresponds to Input"in"(Windows logs) and send them to Output "graylog_udp", i.e. our Graylog.
Save the changes and restart the NXLog service from a PowerShell console opened as administrator (or via the Services console).
Restart-Service nxlogI'd like to take this opportunity to mention the NXLog log file, which can help you if your configuration isn't working. For example, if you don't receive any logs on Graylog...
C:\Program Files\nxlog\data\nxlog.logC. Refine NXLog collection rules
By default, NXLog will send all events from all Windows logs to our Graylog log sink. You can fine-tune NXLog's configuration to send events from certain logs only, or those matching certain criteria.
To do so, please follow this link:
Here's an example, where we modify the Input in NXLog's configuration to transmit only "Security" log events to Graylog.
<Input in>
Module im_msvistalog
<QueryXML>
<QueryList>
<Query Id='1'>
<Select Path='Security'>*</Select>
</Query>
</QueryList>
</QueryXML>
</Input>IV. Receiving Windows logs in Graylog
After configuring Graylog and the NXLog agent on the Windows machine, logs should now be sent to Graylog! To check this, simply click on "Search" in the Graylog menu.
You should see the first logs arriving, which will cause a spike in logs. I recommend that you click on the button highlighted in the image below to refresh the list automatically every 5 seconds (by default).
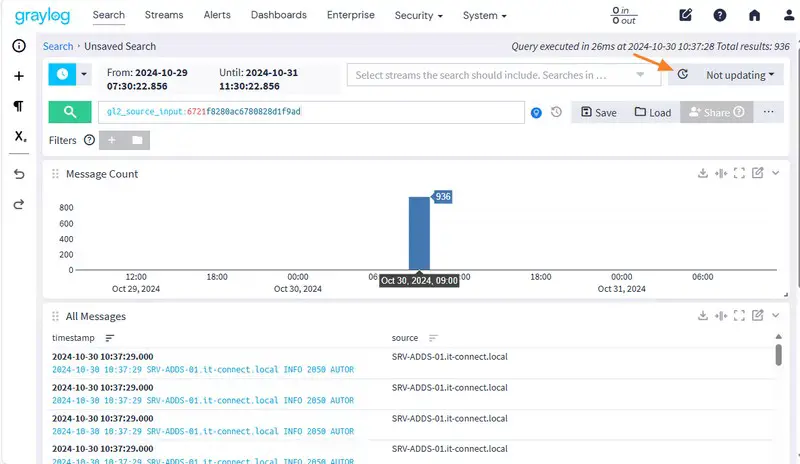
If you click on a log in the list, you can view its contents. This is equivalent to viewing the log from the Windows Event Viewer.
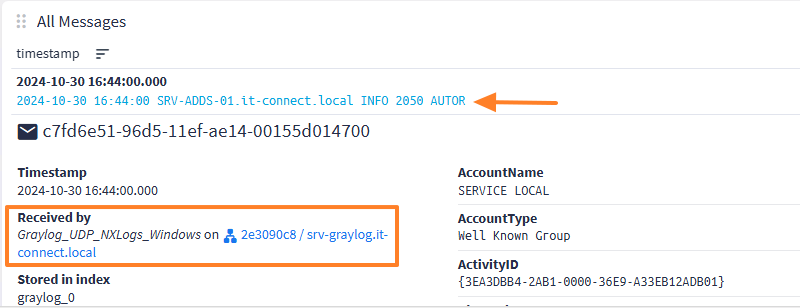
As the logs are stored and indexed in Graylog, the power of the tool lies in its search function. You can enter a filter in the input box to the right of the magnifying glass.
For example, here's how to filter events to display only those with ID 4776 or 4771. This identifies unsuccessful connection attempts on one or more servers. For these events to be generated, you need to adjust the Windows audit strategy.
Here is an example of the results obtained with this query:
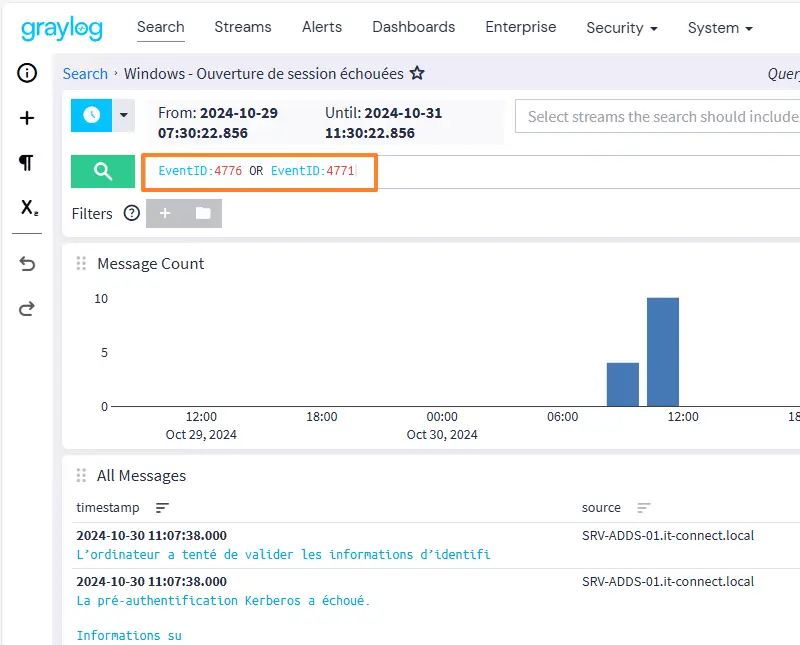
By clicking on the "Save" button on the right, you can save your query for easier retrieval.
In the event of several machines sending logs to Graylog, you can specify the machine name if you wish to analyze the logs of a particular machine. For example, to target the server "srv-adds-01.it-connect.local":
(EventID:4776 OR EventID:4771) AND source:srv-adds-01.it-connect.localNote : the following characters must be preceded by a backslash character: & | : / + - ! ( ) { } [ ] ^ " ~ * ?
To learn more about query syntax, here's a link to the documentation:
V. Deploying NXLog on Windows with a GPO
There are several ways to deploy the NXLog agent and its configuration on multiple machines. In addition to the Group Policy Organization (GPO) method we'll discuss below, you can also use Intune or other solutions such as Ansible and Puppet.
The installation of NXLog is based on two elements: the MSI installation package, which represents the application itself, and the ".conf" configuration file, which configures the sending of logs to Graylog. We therefore need to install the application and copy the configuration.
To install NXLog by GPO, it is possible to use a "Software installation" type GPO. In this case, a GPO should be set up to install the agent, and when it's installed, another GPO should be activated to push the configuration. I've noticed that if the configuration file is pushed before the installation, it doesn't work properly...
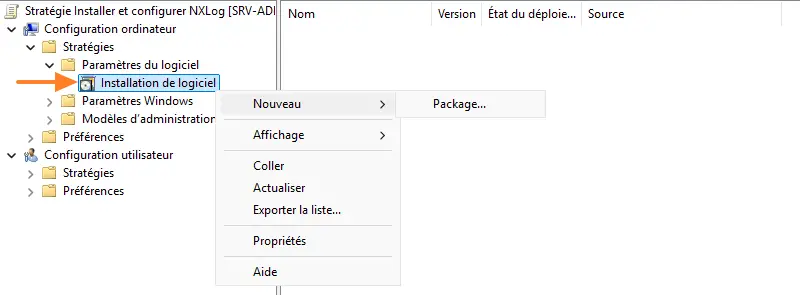
The method chosen and described in this article is based on the use of a PowerShell script. It will install NXLog, copy the configuration file(s) (as there may be several) and restart the service to apply the changes.
A. The nxlog.d directory
The NXLog agent relies on a main configuration file simply named "nxlog.conf", located in the agent's "conf" directory. Within this "conf" directory, there is another, empty directory called "nxlog.d". It's intended for loading other configuration files!
The default configuration file is configured to load ".conf" files stored in this directory using these two lines:
define CONFDIR %ROOT%\conf\nxlog.d
include %CONFDIR%\\*.confThis means you can create several different configurations (depending on your needs, server roles, etc.) and copy your configuration files to the "nxlog.d" directory. This mechanism makes configuration much more flexible.
In this example, the "windows.conf" file will be copied and pasted by GPO into the "nxlog.d" directory. It contains only this content (which is no longer useful in the main config file):
# Retrieve event viewer logs
<Input in>
Module im_msvistalog
<QueryXML>
<QueryList>
<Query Id='1'>
<Select Path='Security'>*</Select>
</Query>
</QueryList>
</QueryXML>
</Input>
# Declare Graylog server (according to input)
<Extension gelf>
Module xm_gelf
</Extension>
<Output graylog_udp>
Module om_udp
Host 192.168.10.220
Port 12201
OutputType GELF_UDP
</Output>
# Routing flows in to out
<Route 1>
Path in => graylog_udp
</Route>B. Installation sources
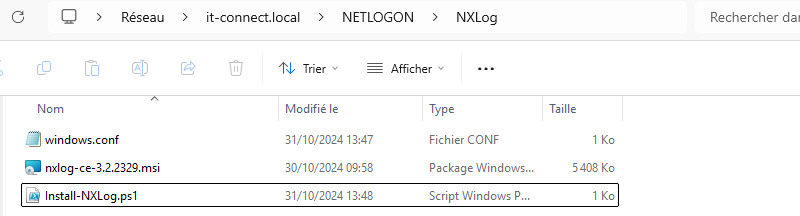
You need to centralize the installation sources on a share accessible by the machines in your Active Directory domain. In this example, the "NETLOGON" share (from SYSVOL) will be used. In this example, you'll find the MSI package, the "windows.conf" configuration file and the PowerShell script named "Install-NXLog.ps1".
Here are the contents:
C. PowerShell script to install NXLog
Below is the code for the PowerShell script that will be used to install the NXLog agent on Windows machines. Although the code is indicated in the body of the article, I invite you to retrieve it directly from our GitHub.

function Install-NXLog {
param (
[Parameter(Mandatory=$true)][string] $MsiPath,
[Parameter(Mandatory=$true)][string] $ConfigPath
)
$NXLogConfigPath = "C:Program Filesnxlogconfnxlog.d"
$NXLogExePath = "C:Program Filesnxlognxlog.exe"
if ((Test-Path $MsiPath) -and (-not (Test-Path $NXLogExePath))) {
& msiexec.exe /quiet /i $MsiPath
Start-Sleep -Seconds 30
}
if ((Test-Path $ConfigPath) -and (Test-Path $NXLogConfigPath)){
Get-ChildItem -Path $ConfigPath -Filter "*.conf" | Foreach{
Copy-Item $_.FullName -Destination $NXLogConfigPath -Force
}
}
$NXLogService = (Get-Service -Name nxlog -ErrorAction SilentlyContinue)
if ($NXLogService) {
Restart-Service -InputObject $NXLogService
}
}
Install-NXLog -MsiPath "\\it-connect.local\NETLOGON\NXLog\nxlog-ce-3.2.2329.msi" `
-ConfigPath "\\it-connect.local\NETLOGON\NXLog"This script will perform the following actions:
- Install the NXLog application, once only, as we check the presence of the "nxlog.exe" file on the machine before installing it.
- Copy the configuration files from the source directory (-ConfigPath) to the "nxlog.d" directory of the NXLog agent, each time the script is run. This may allow you to add files over time.
- Restart nxlog service to load configuration files.
Alternatively, you could use this script only to perform the installation and use a Preferences GPO to copy the configuration files. This would have the advantage of using targeting to copy a configuration file according to one or more criteria. For example, only on machines belonging to a specific security group.
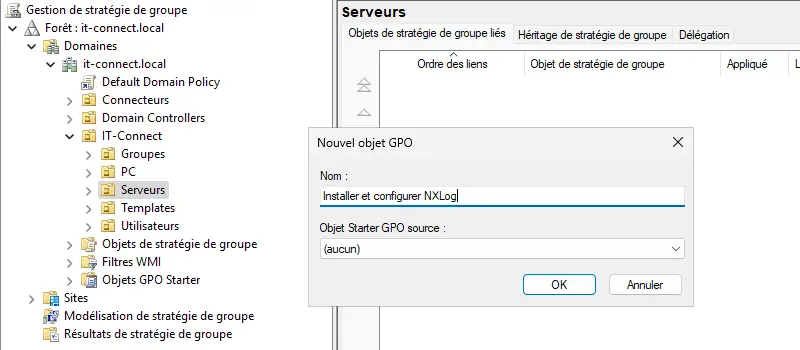
D. Create GPO for NXLog
From the "Group Policy Management" console, create a new Group Policy and link this GPO to your OUs as required. Here, the GPO is called "Install and configure NXLog" and will be linked to the organizational units named "Domain Controllers" and "Servers".
Next, modify the GPO, and add a new PowerShell startup script :
1 - Go to the following location: Computer configuration > Windows settings > Scripts (start/stop) > Startup
2 - Click on the "PowerShell Scripts" tab
3 - Click on the "Add" button
4 - Add your script, making sure to specify a network path (UNC path)
5 - Confirm.
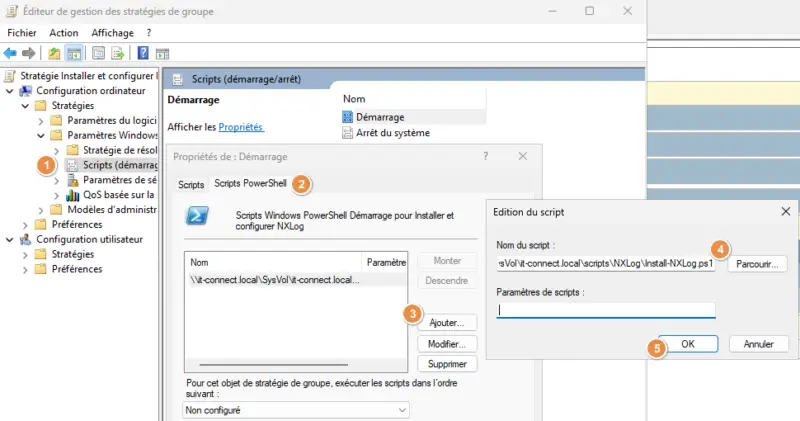
For my part, the network path to access the script is :
\\it-connect.local\SysVol\it-connect.local\scripts\NXLog\Install-NXLog.ps1E. Test configuration
All that's left is to test it on a machine! A "gpupdate" and a reboot are in order...
The NXLog agent has been installed and the configuration file has been copied! This is great news.
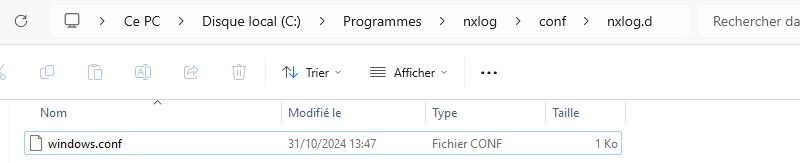
There's also news from Graylog, as new Windows Server machines are transmitting their logs.
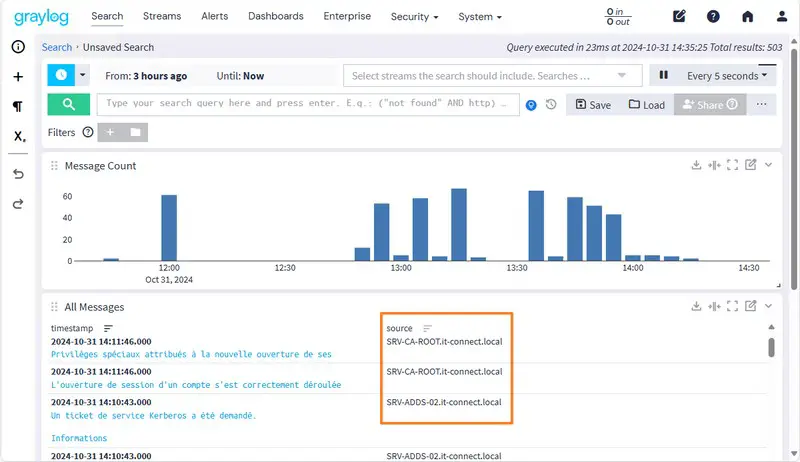
VI. Conclusion
Thanks to this tutorial, you should be able toinstall and configure NXLog on Windows to send your logs to the Graylog log sink! In an Active Directory environment, you can also use this tutorial to deploy NXLog on several servers and/or workstations.
To take this a step further, you can couple the use of Graylog and NXLog with Sysmon to enrich the Windows logs and provide even more relevant feedback to Graylog. In this case, the configuration of Graylog and NXLog is identical, but Sysmon will generate additional events. It will also add additional information, including the MITRE's TTP identifiers, to link an event to a - potentially - malicious action.
In the next Graylog tutorial, we'll look at how to send logs from Linux to Graylog.
 www.it-connect.fr
www.it-connect.fr









