Linux: how to calculate SHA-1, SHA-256 and SHA-512 fingerprints?
Table of Contents
I. Introduction
In this tutorial, we'll learn how to calculate a SHA-1, SHA-256 or SHA-512 fingerprint under Linux. This method lets you calculate and control the fingerprint of a file or string via three dedicated commands, available on most Linux systems.
It's worth noting that the SHA-1 hash algorithm is neither the most recent nor the most robust. Although more secure than the well-known MD5, it is now preferred to SHA-256 or even SHA-512. The latter generate fingerprints with more bits, respectively 256 (32 bytes) and 512 bits (64 bytes), compared with 160 bits for SHA-1. This contributes to their greater robustness and reduces the risk of collisions.
For this reason, SHA-256 and SHA-512 are now widely preferred. However, they are not infallible and could be vulnerable in the long term to advances in cryptanalysis and quantum computing.
But what is a footprint, and why is it so important? Let's start with a quick reminder.
II. Reminder: what is a hash?
A hash, also known as a cryptographic fingerprint or checksum, is a unique sequence of characters generated from a piece of data (text or file). It is used to verify the integrity of a file or text: if a single bit changes, the hash will be completely different.
Integrity checks are used in many contexts, but mainly for cybersecurity purposes. The aim is to verify that a file has not been modified since a last-known situation, or that it has not been altered during transfer. Just like our fingerprints, a file's fingerprint is supposed to be unique.
Now that we've had a quick reminder, let's see how to check a file's fingerprint under Linux.
III. Using shaXsum commands to calculate a footprint under Linux
We will use the sha1sum, sha256sum and sha512sum to generate file fingerprints under Linux. This will enable the use of SHA-1, SHA-256 or SHA-512 algorithms depending on the application. The choice of algorithm can be guided by security and performance requirements.
Here are some practical examples of how to calculate the fingerprint of a file using the SHA-1, SHA-256 and SHA-512 hash algorithms:
# Calculate the SHA-1 fingerprint of a file
$ sha1sum document.txt
3d2636af5068b1af3199ee1d3f3796a348339d2f document.txt
# Calculate the SHA-256 fingerprint of a file
$ sha256sum document.txt
12a1f36c7d1b4ece74ce916e126d99515b750c3066e08ef3536e14cefde42108 document.txt
# Calculate the SHA-512 fingerprint of a file
$ sha512sum document.txt
8ca31053f0349f3161980db84e97462e0e263b69de3740c6cac5aa6d66f96943cfe2953904cb8c515be847a755cd563ada3698ff515667a936355db820303696 document.txtAs you can see, the hashes produced are of different lengths, and these three commands are used in the same way. We can, for example, use them to check the integrity of two or more files, in particular to compare them :
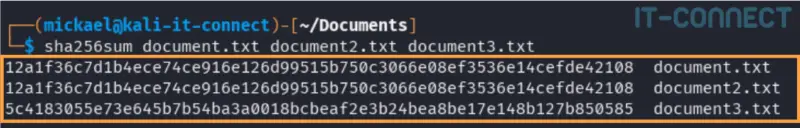
In this example, in which we use SHA-256, the first two files are identical (same SHA-256 hash generated), but the third is different.
Alternatively, you may wish to save the fingerprint in a file so that users can compare it again. Typically, fingerprints are stored in a file with the extension .checksum :
$ sha256sum document.txt
12a1f36c7d1b4ece74ce916e126d99515b750c3066e08ef3536e14cefde42108 > documents.txt.checksumFinally, we can calculate the fingerprint of a string as follows:
$ echo "This is a string." | sha256sum
151c792da29674e1f697191ef58544a18943395b86b33c211aafddffa2cbce83 -IV. Checking file integrity under Linux
Now let's try a little integrity checking with one of the three commands we've just seen. Go to the VirtualBox download page and download any version of the installer.
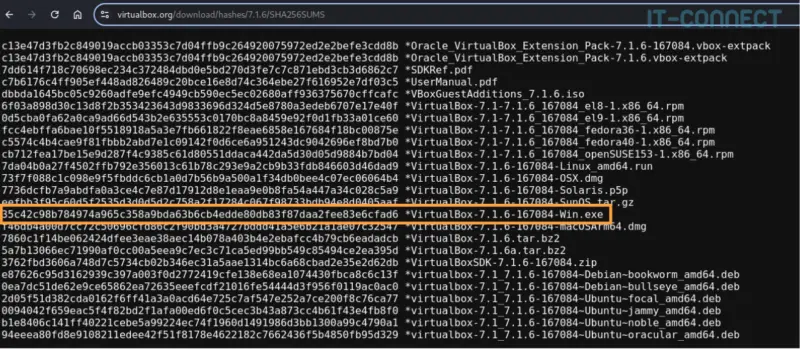
You'll also notice a link to "SHA256 checksums", which contains the hashes for each of the proposed files. For example, I downloaded the Windows installer whose checksum is 35c42c98b784974a965c358a9bda63b6cb4edde80db83f87daa2fee83e6cfad6.
Once the file is downloaded, I check its integrity with the command sha256sum :
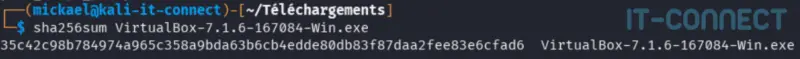
SHA-256 fingerprints are the same. I can conclude that the file is intact, confirming that it has not been altered during transfer.
V. Conclusion
You can now easily calculate the SHA1, SHA-256 and SHA-512 fingerprint of a file or string. This is particularly useful for calculating file integrity.
I invite you to consult our many other tutorials on Linux and its commands. : IT-Connect.tech - Linux
 www.it-connect.fr
www.it-connect.fr









