How to configure a Fine Grained Password Policy on Windows Server ?
Table of Contents
I. Introduction
In this tutorial, we'll look at how to set up a fine-tuned password policy (PSO) on Windows Server 2022, with the aim of having multiple password policies applicable to Active Directory security groups.
By default, the " Default Domain Policy " Group Policy Object (GPO) contains settings to define a password complexity and account lock policy for the Active Directory domain.
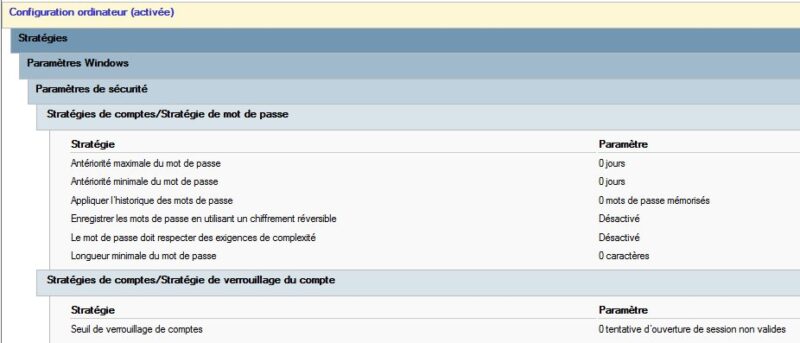
However, since Windows Server 2008, then Windows Server 2008 R2 and now Windows Server 2022, it has been possible to create what is known as a "Fine Grained Password Policy". The advantage of this system is that you can create several password complexity and account locking policies, and then apply them only to certain objects.
These refined password policies allow greater flexibility in password and account lock management, as they can be applied across security groups. For example, company accountants can be required to use a password of at least 16 characters, and secretaries a password of at least 10 characters. This is also a way of protecting accounts belonging to the "Domain Admins" group with a very strict password policy, within the limits of the possibilities offered by refined password strategies.
In this example, we're going to create a refined password policy that will apply to members of the "Accounting" group, but the process applies to whatever you want! This tutorial is compatible with other versions of Windows Server, including Windows Server 2025.
II. The refined notion of password strategy
Refined password strategies correspond to "Password Settings Objects" and are also called "PSO".
- PSO (Password Settings Object):
- PSC (Password Settings Container): Password Settings Container
A PSO can be applied directly to a user, but also to a group, which is more interesting in terms of administrative flexibility.
A user/group can be linked to several SOPs, but in the event of a SOP conflict, a priority attribute called "precedence value" is used to define a priority for applying the strategy.
In the absence of a PSO policy, the domain password policy applies.
To use this feature, the functional level of your domain and forest must be at least "Windows Server 2008". The good news is that since Windows Server 2012, Microsoft has simplified the management of refined password policies.
III. Creating a refined password policy
On your domain controller, open the " Active Directory Administration Center ", which can be accessed from Administrative Tools or via " dsac.exe ".
Choose the tree view on the left, scroll down to your domain name, then " System " and " Password Settings Container ".
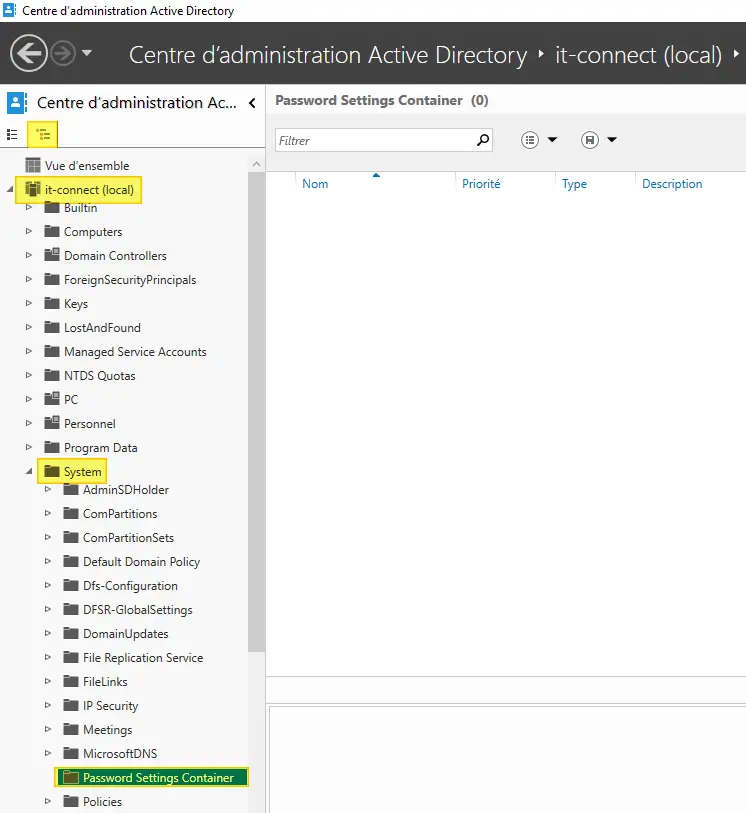
In the right-hand pane, click on " New " and then " Password settings " as follows:
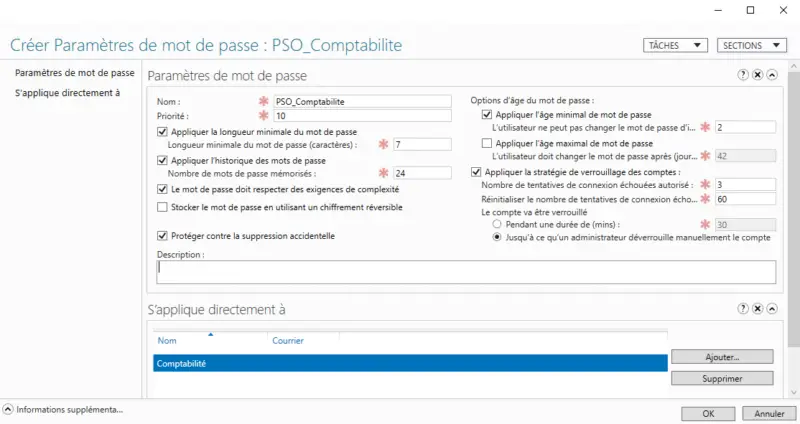
A complete form appears on the screen: now you'll have to fill it in. As I do things well, here are a few pointers to help you:
- Name: Policy name, in my case "PSO_Comptabilite".
- Priority: Value greater than 0, used to arbitrate in the event of conflict between two SOPs applied to the same object. Remember to space out the values of your different SOPs so you can play with priorities easily.
There are two rules to follow:
- The lower value will take precedence over the higher value.
- In the event of identical priorities, the policy with the lowest GUID will be applied.
- A PSO applied at user level has priority at group level.
Let's move on.
- Apply minimum password length: whole number to define minimum password length. Let's use 16 characters for this example.
- Apply password history: sets the number of old passwords that a user cannot reuse, forcing them to "invent" a new password a certain number of times. By default, the value is 24, which seems quite correct to me.
- Password must meet complexity requirements: indicate whether or not the password must meet these requirements (recommended for security reasons).
- Store password using reversible encryption: it's best not to activate this option, again for security reasons. Enabling this option means that the password stored in the AD can be retrieved in clear text, which is not desirable.
- Protect against accidental deletion: protects against unintentional deletion of this PSO object.
- Apply minimum password age: the minimum lifetime of a password, preventing a user from changing his password several times in succession. This could allow him to exceed the password history limit and redefine his initial password...
This value must correspond to a number of days.
- Apply maximum password age: same principle as the previous parameter, but for the maximum lifetime. If we refer to ANSSI recommendations, we shouldn't impose an expiry date on passwords for non-sensitive accounts (without elevated privileges), if the overall policy is robust enough. I uncheck this option.
- Authorized number of failed attempts: once the authorized number of attempts has been exceeded, the account will be locked automatically. This prevents brute-force attacks, where numerous attempts are made...
- Reset number of failed connection attempts after (mins): once this time has elapsed, the number of failed attempts is reset to zero.
Let's take an example: you set the "Number of failed attempts allowed" parameter to "3" and the "Reset number of failed login attempts after (mins)" parameter to 60 minutes . Once the user has entered the wrong password once, a 60-minute countdown will start, and if within this 60-minute period the user makes 2 further failed attempts (bringing the total to 3), the account will be locked. On the other hand, if after 60 minutes there have been no further failed attempts (or only one, i.e. 2), the counter is reset to zero. This parameter is essential, as without it, the number of failed attempts would never be reset to zero, and the user account would be locked if the counter kept incrementing.
- The account will be locked:
When an account is locked, it can be :
- For a period of (mins): set a lock value for the account, which will be automatically unlocked once the timeout has elapsed.
- Until an administrator manually unlocks the account: manual action by an administrator is required to unlock the account.
As for the "Applies directly to" section, you need to add the users and/or groups to which you wish to apply this PSO strategy. To do this, click on the "Add" button in the bottom right-hand corner. For my part, I'm adding the group named "Accounting", and I recommend that you use group management rather than user management.
In the end, I get the following configuration:
For your information, each PSO object contains specific attributes belonging to the msDS-PasswordSettings class and containing the values defined when the policy was created. For example: msDS-LockoutDuration, msDS-LockoutThreshold and msDS-MaximumPasswordAge.
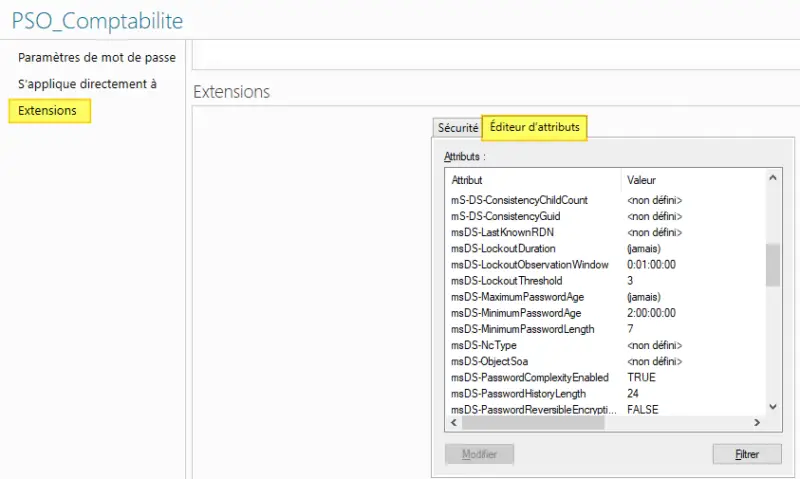
Click " OK" when you're finished.
You can now set up a refined password strategy within your Microsoft infrastructure. You can create several and apply them to different groups.
IV. What refined password policy applies to my user?
If you want to see which policy applies to a user, always in the "Active Directory Administration Center"select " Users " in the tree structure. Then find your user in the list, select him/her and click on " View password settings " on the right.
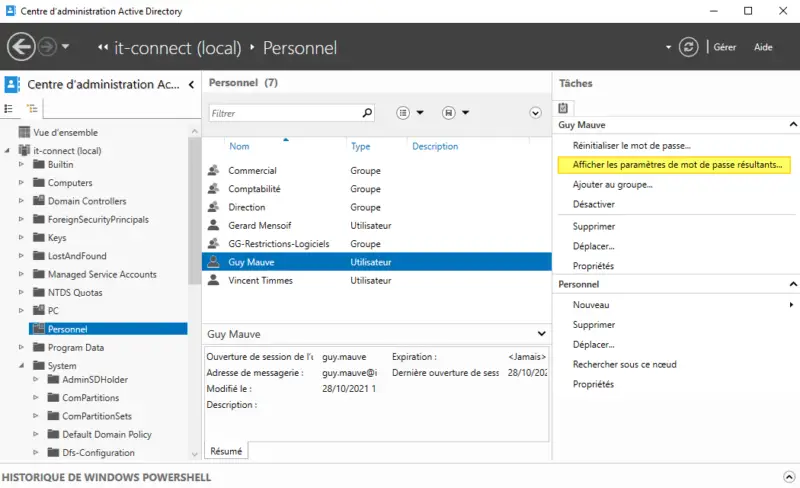
A window will open and you'll have the answer to your question!
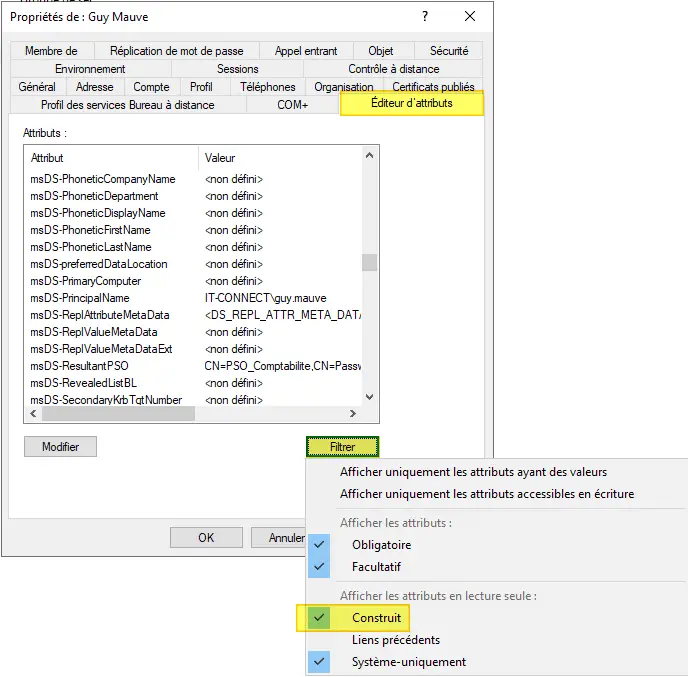
Another way is to use the "Active Directory Users and Computers" console. Then activate the advanced view to access the attribute editor (View > Advanced features).
Find your user, right-click on properties and click on the "Attribute Editor" tab. Then click on the "Filter" button and click on "Built" to display the msDS-ResultantPSO attribute.
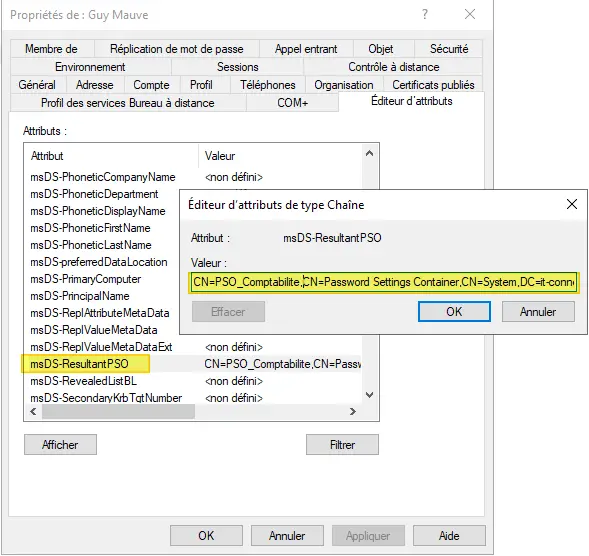
If you search for this attribute and look at its value, you can see the name of the policy that applies. For example, I get :
CN=PSO_Comptabilite,CN=Password Settings Container,CN=System,DC=it-connect,DC=local
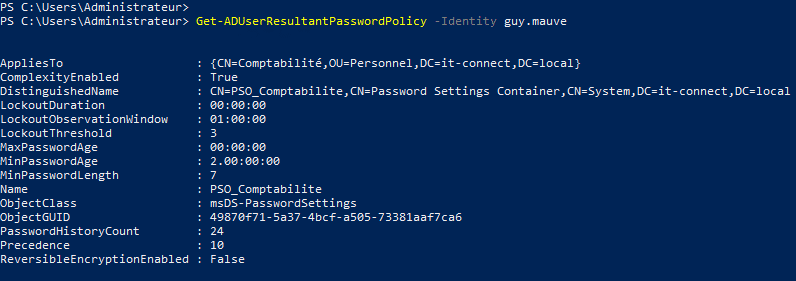
But in the end, PowerShell and the "Get-ADUserResultantPasswordPolicy" cmdlet make things even simpler, since all you have to do is specify the user's ID:
Get-ADUserResultantPasswordPolicy -Identity guy.mauve
The"Name" property gives us the policy name directly.
Let's keep the momentum going and learn how to create a refined password policy with PowerShell.
V. Creating a refined password policy with PowerShell
PowerShell provides a set of cmdlets for managing PSOs from the command line. This can be useful if you have a large number of policies to create, or if you want to have a ready-to-use script to deploy to your customers.
There are several pretty cool cmdlets built directly into PowerShell's Active Directory module:
- New-ADFineGrainedPasswordPolicy: create a new refined password policy
- Add-ADFineGrainedPasswordPolicySubject: assign a policy to a group or user
- Set-ADFineGrainedPasswordPolicy: modify an existing policy
- Get-ADFineGrainedPasswordPolicy: list refined password policies for your Active Directory domain
To create a new refined password policy with New-ADFineGrainedPasswordPolicy, you're going to have to use a lot of parameters. This is not surprising, as there are a lot of fields when you do it via the GUI.
Before you start, please note that time values must follow a specific format: D.H:M:S.F, i.e.: Day.Hours:Minutes:Seconds:Fractions of a second (optional).
The command below creates a policy named"PSO_ComptabiliteBis" with the following options:
- A priority of 10 (-Precedence)
- Minimum password length of 7 characters (-MinPasswordLength)
- A history of the last 24 passwords (-PasswordHistoryCount)
- Reversible encryption disabled (-ReversibleEncryptionEnabled)
- Password complexity required (-ComplexityEnabled)
- Lockout threshold set at 3 failures (-LockoutThreshold)
- Reset number of failed connection attempts after 60 minutes (-LockoutObservationWindow)
- Lock account for 60 minutes (-LockoutDuration)
- Password must be kept for at least 1 day (-MinPasswordAge)
- Password never expires (-MaxPasswordAge)
- PSO object is protected against accidental deletion (-ProtectedFromAccidentalDeletion)
This gives the following command:
New-ADFineGrainedPasswordPolicy -Name "PSO_ComptabiliteBis" -DisplayName "PSO_ComptabiliteBis" ` -Precedence 10 -MinPasswordLength 7 -PasswordHistoryCount 24 ` -ReversibleEncryptionEnabled $false -ComplexityEnabled $true ` -LockoutThreshold 3 -LockoutObservationWindow "0.01:00:00" ` -LockoutDuration "0.01:00:00" -MinPasswordAge "1.00:00:00" ` -MaxPasswordAge "0.00:00:00" -ProtectedFromAccidentalDeletion $true
If you want to activate the"Account will be locked until an administrator manually unlocks the account" option via PowerShell, it's a bit complicated (not to say impossible). To do this, you need to set "-LockoutDuration" to"0.00:00:00", except that the parameter can't have a value lower than"-LockoutObservationWindow", so this is bound to cause problems! The problem is the same if you create the policy and then try to modify it, you get the error"New-ADFineGrainedPasswordPolicy: Modification has not been authorized for security reasons".
Note: to modify an existing policy, use the command "Set-ADFineGrainedPasswordPolicy -Identity <name-PSO>" followed by the parameter(s) to be modified.
For detailed information on each parameter of the New-ADFineGrainedPasswordPolicy command, go to this page :
Next, to assign the new "PSO_ComptabiliteBis" policy to our "Accounting" group, we will perform the following command:
Add-ADFineGrainedPasswordPolicySubject"PSO_ComptabiliteBis" -Subjects"Comptabilité"(Accounting)
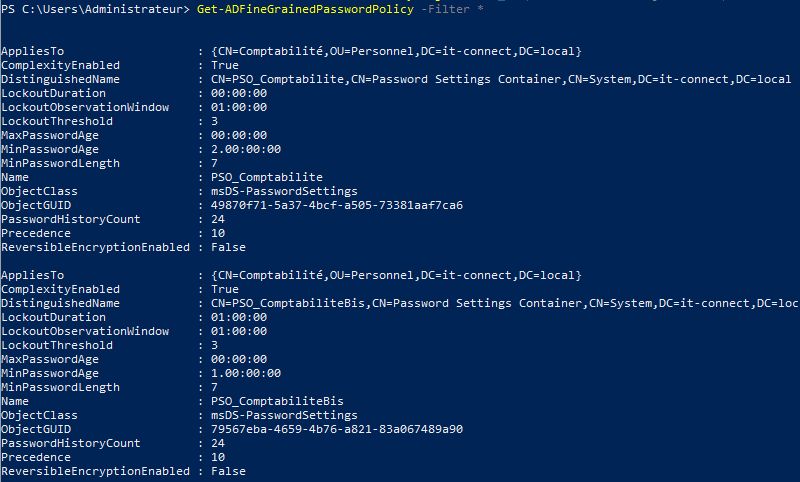
Finally, you can list your PSOs at any time with this command:
Get-ADFineGrainedPasswordPolicy -Filter *
For example:
With these few commands, you'll be able to manage your refined password policies with PowerShell!
VI. Further information
To go further than what Microsoft offers natively with Active Directory, there are third-party tools available, notably from Specops. I've had the opportunity to use two Specops programs:
A free tool that analyzes your Active Directory passwords (via hash) to detect vulnerable passwords and check your password policies for compliance with best practices.
Find out more by watching the video below or by reading my tutorial dedicated to this software.
Specops also offers a paid-for tool that lets you set up highly refined password policies, going much further than what Microsoft offers natively.
Find out more in the video below, or via my tutorial on this software.
 www.it-connect.fr
www.it-connect.fr









