Active Directory: 4 free and effective password auditing tools
Table of Contents
I. Introduction
What tools can be used to audit Active Directory passwords? That's the question we're going to answer in this article.
In an Active Directory environment, password management is essential, as weak or compromised passwords can lead to account compromise. These accounts, which are difficult to identify without an audit, open the door to a variety of attacks, including dictionary attacks (brute force, credential stuffing).
We'll just mention a few free tools, some of which are accessible from the command line, notably those based on PowerShell, and a more comprehensive tool with a graphical interface and the ability to generate a ready-to-use report.
If you're interested in the subject of AD passwords, I recommend you read the following article to complement this one:
II. Specops Password Auditor
The first tool we're going to talk about is a benchmark in Active Directory password auditing. Developed by Specops Software several years ago, Specops Password Auditor is a simple, effective tool. Beyond the analysis, which in many respects is similar to the tools we'll discuss later, its great strength is the ready-to-use report it is able to generate.
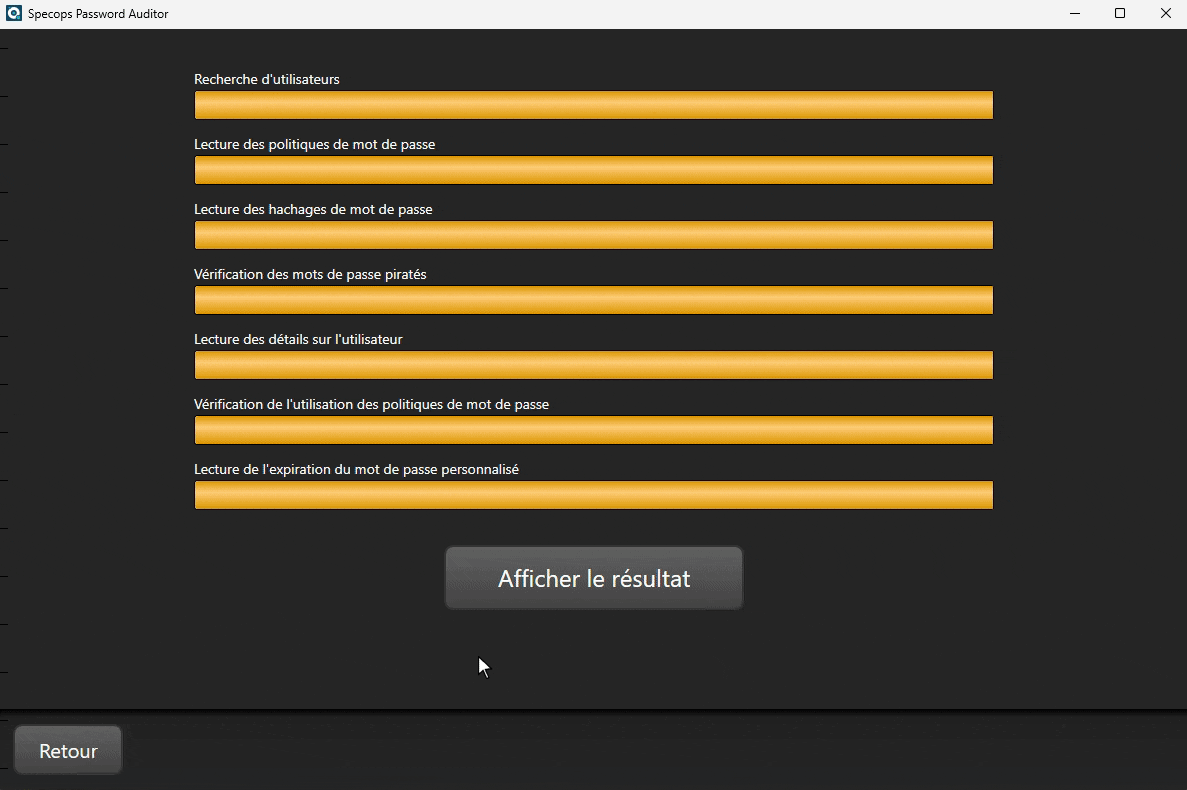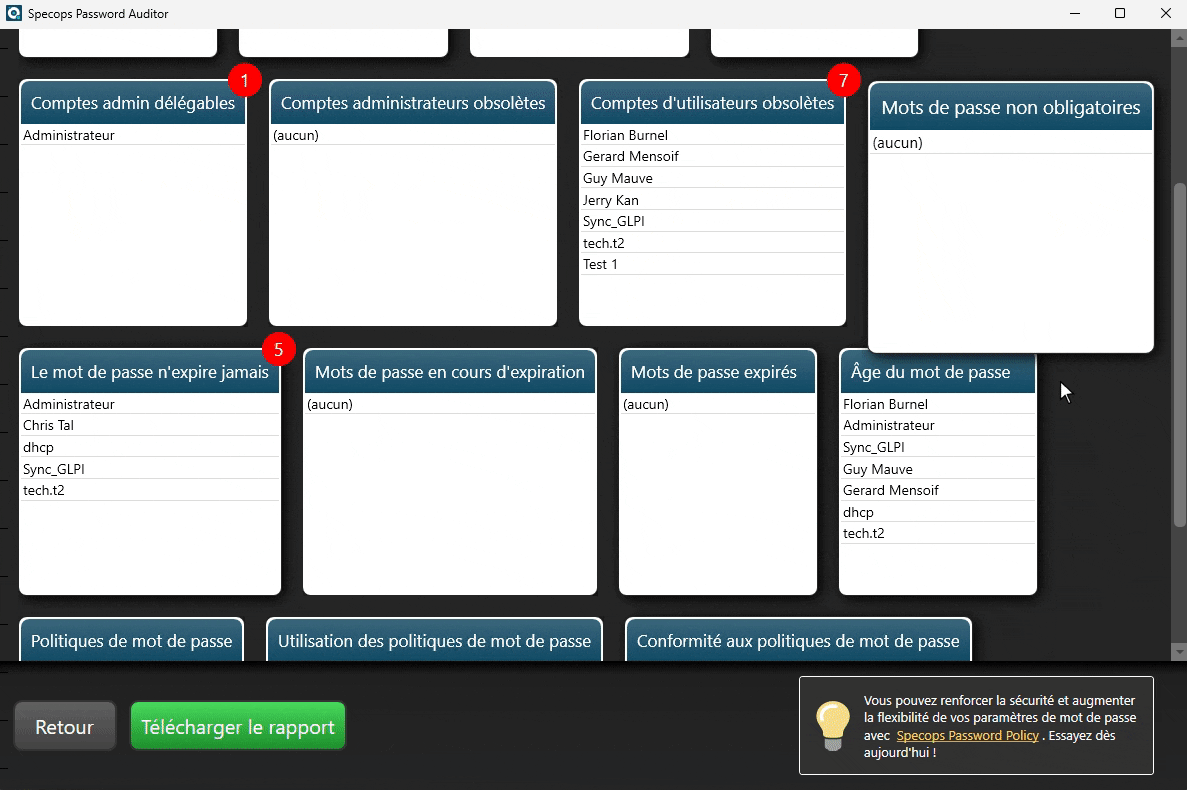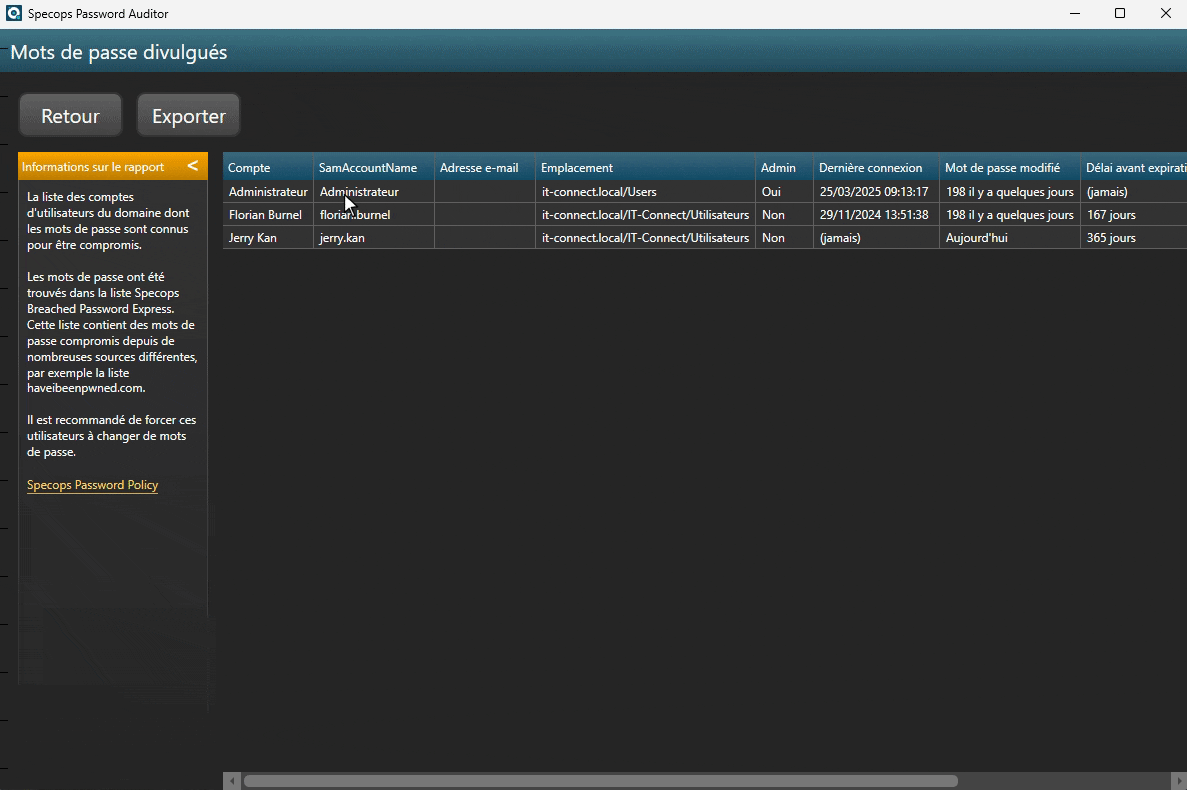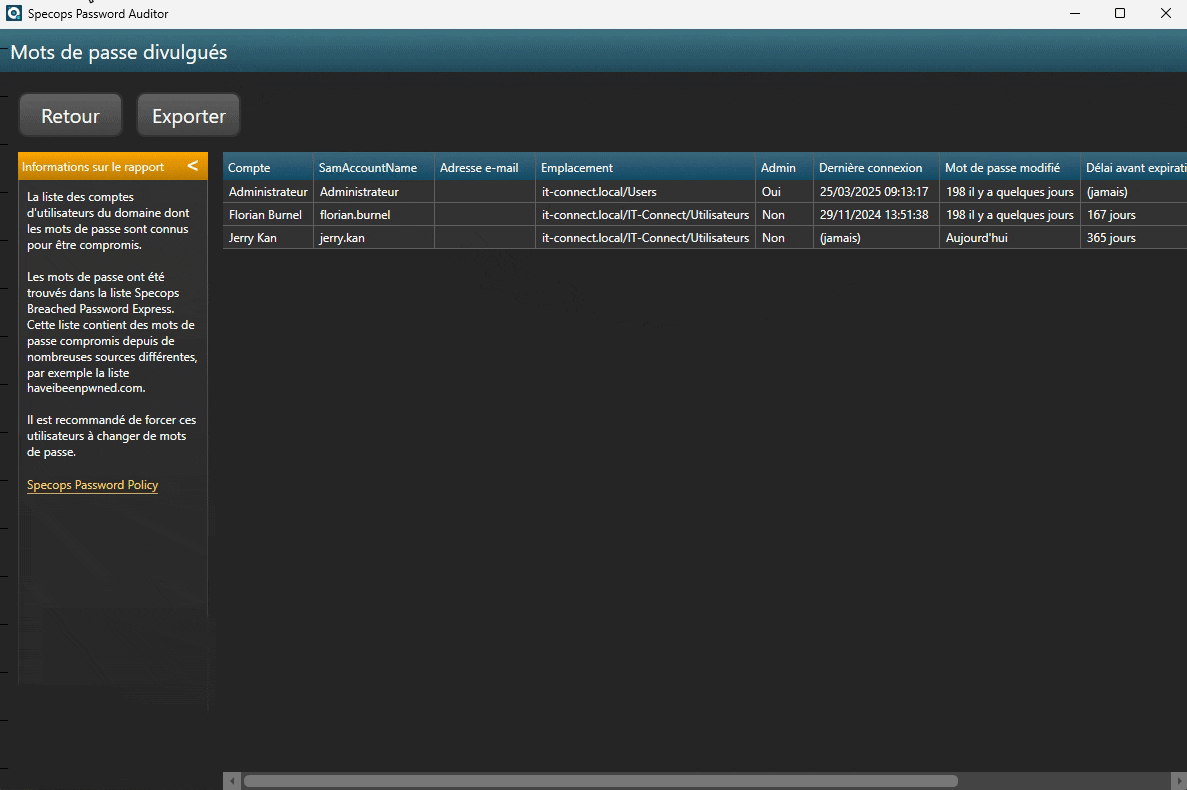
This free software is capable of detecting compromised passwords used by your Active Directory users. To do this, it relies on a locally downloaded password database: the current version contains over 1 billion passwords. It also relies on password hashes for comparison, as do other tools of this type.
You can download the tool here:
It takes just a few minutes to generate the report shown below. This report in French (or in another language) is ready to be presented to the information system (IS) management or to the person in charge of IS security. This is a real time-saver compared with the 3 other tools presented in this article, as they don't have this "reporting" dimension.
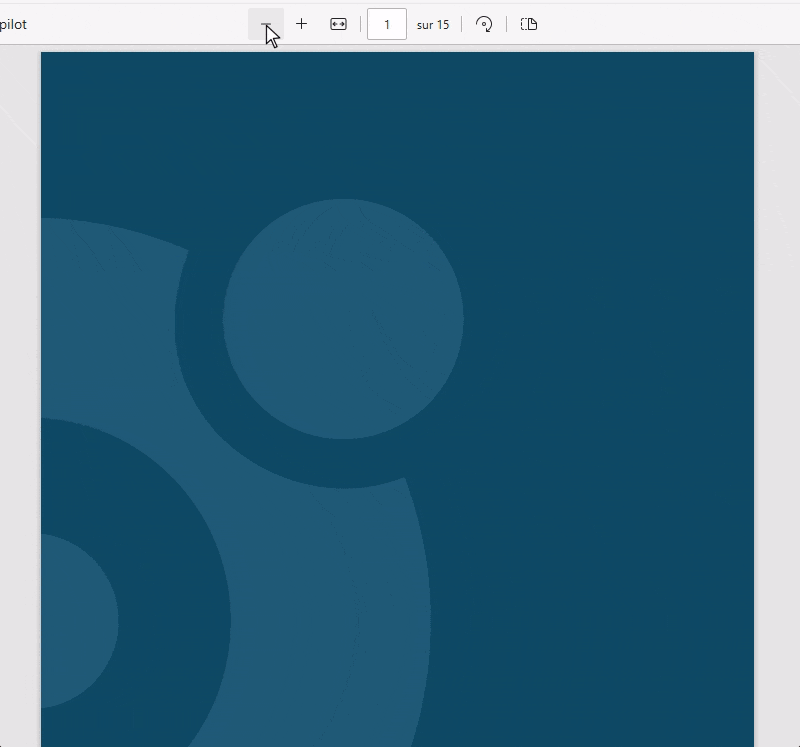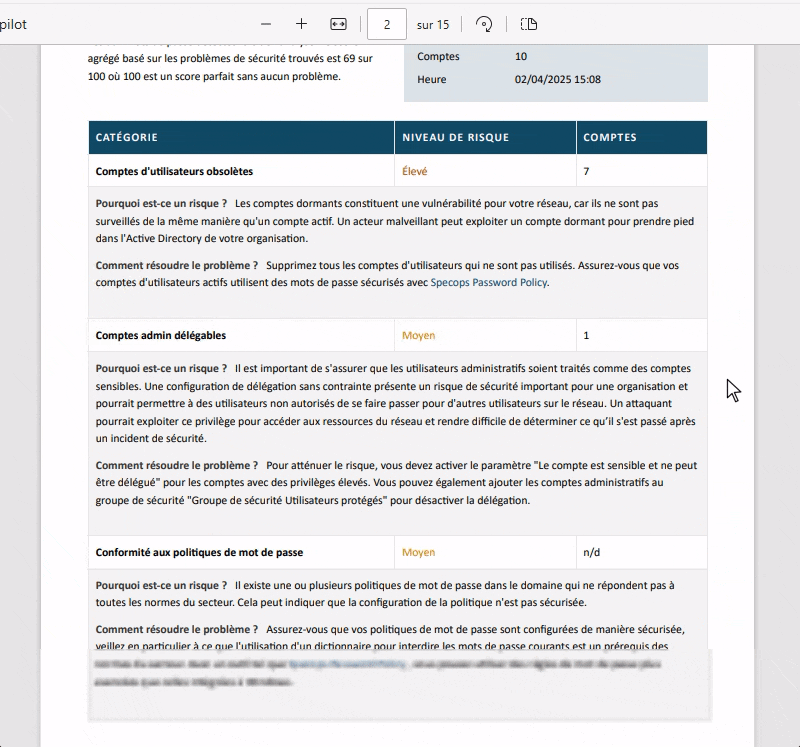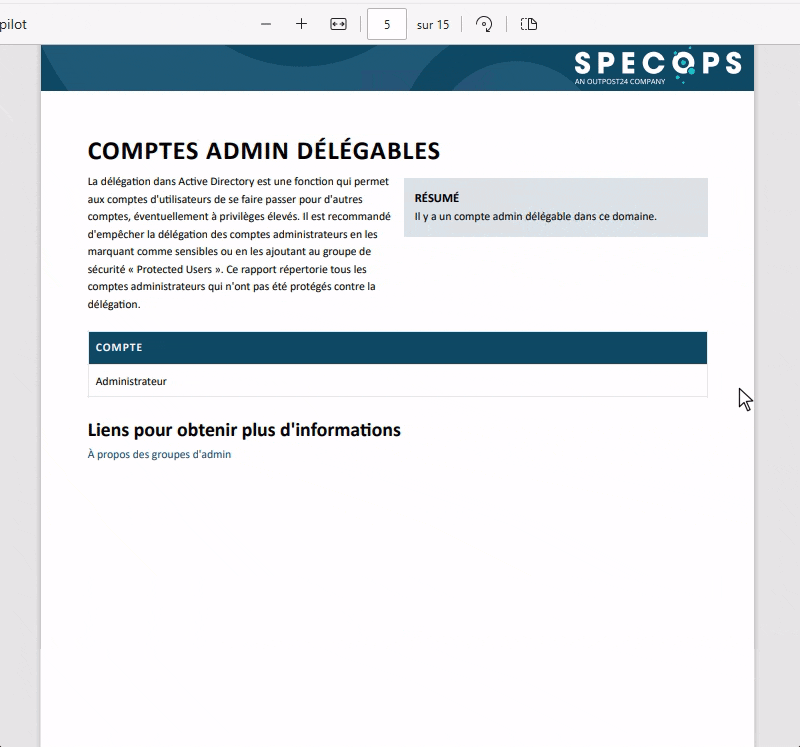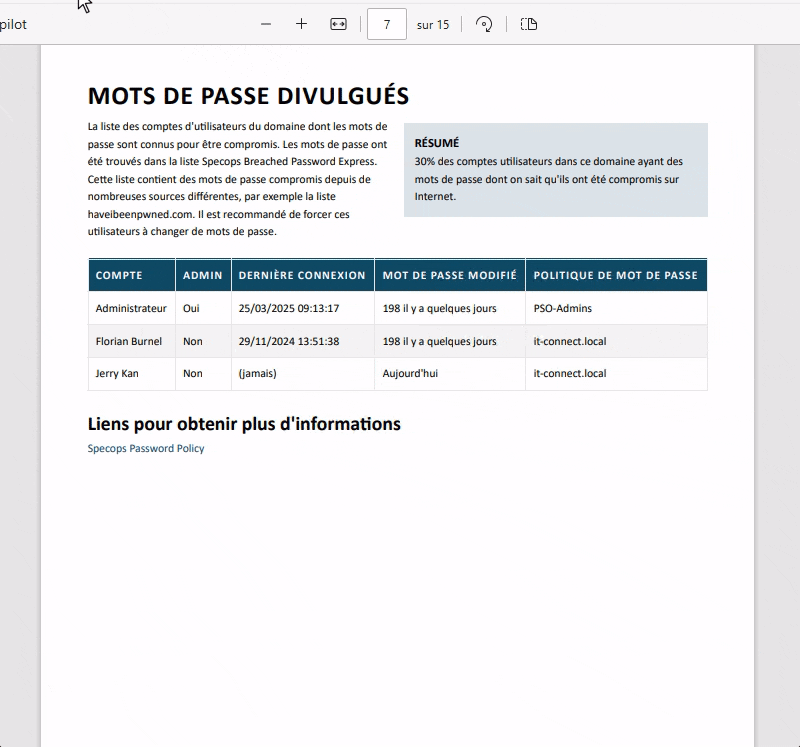
Specops Password Auditor analyzes the following security points:
- Password policy compliance (ANSSI, CNIL, NIST, BSI, etc.)
- Accounts with empty passwords
- Accounts with leaked passwords (compromised passwords)
- Accounts with identical passwords
- Domain administrator accounts
- Administrator accounts not protected against delegation
- Inactive administrator and user accounts
- Accounts where password is not required
- Accounts where the password never expires
- Accounts where the password is set to expire
- Accounts with expired passwords
- Password age for each user/administrator account
- List of password policies with key characteristics (including entropy)
- Use / assignment of password policies
In addition to the full report, you can export each user list as a text file in CSV format. This can enable you to apply further processing to accounts affected by a specific security problem.
This application has already been the subject of a full presentation on IT-Connect, as well as a video. Here are the corresponding contents:
To benefit from in-depth, automatic and proactive analysis, you need to upgrade to the pay-as-you-go solution called Specops Password Policy. It is also associated with a larger database containing more than 4 billion passwords.
III. DSInternals
From now on, we'll switch to the PowerShell command line. We'll give pride of place to the PowerShell module DSInternalswhich has a very good reputation and has been tried and tested for years. It's a versatile module, and particularly relevant for everything to do with Active Directory password security. In particular, there's a cmdlet called Test-PasswordQuality able to perform a quality test of Active Directory passwords.
This tool analyses the following points:
- Passwords stored with reversible encryption
- Presence of LM (LanMan) password hashes
- Accounts without defined password (empty password)
- Passwords found in a dictionary (weak or compromised passwords)
- Accounts using the same password
- User accounts with SamAccountName as password
- Computer accounts with default passwords
- Lack of Kerberos AES keys for some accounts
- Accounts not requiring Kerberos authentication (Kerberos pre-authentication)
- Accounts authorized to use DES encryption only
- Accounts vulnerable to Kerberoasting attacks
- Administrative accounts (current or former) authorized for delegation
- Accounts whose password will never expire
- Accounts for which a password is not required
- Accounts that require smart card authentication, but still have a password
We can see that the analysis is comprehensive and covers a multitude of potential weaknesses. Active Directory analysis can be carried out online or offline from a base file. ntds.dit.
Without further ado, install the PowerShell :
Install-Module DSInternals -ForceThen, to use the DSInternals module, you have two options:
- Use a password dictionary to see if certain users are using a password in the dictionary.
- Do not use a dictionary
The first option opens the door to the detection of compromised passwords using a list of passwords. This may be a password database you have compiled yourself, or a dictionary corresponding to a data leak. A good example is the RockYou password database, version 2024 of which contains over 10 billion passwords... But beware of the computing power required to perform the analysis.
Here, we'll simply use a file named passwords.txt with these values :
IT-Connect
TutorielInformatique
P@ssword!
azertyuiop
azerty1234!
ActiveDirectory@AuditThere are therefore three variables to define:
# The path to the password dictionary file
$DictionaryFile = "C:TEMPpasswords.txt"
# The name of the domain controller to be queried
$DC = "SRV-ADDS-01.it-connect.local"
# The area in which the objects to be searched are located
$Domain = "DC=it-connect,DC=local"
We'll use the PowerShell cmdlet Get-ADReplAccount to read the contents of the AD directory database and retrieve the list of objects and their secret attributes. For each user, including those disabled, we'll evaluate the password.
Here is the command:
Get-ADReplAccount -All -Server $DC -NamingContext $Domain | ` Test-PasswordQuality -WeakPasswordsFile $DictionaryFile -IncludeDisabledAccounts
This command will return a report to the console with the result for each point.
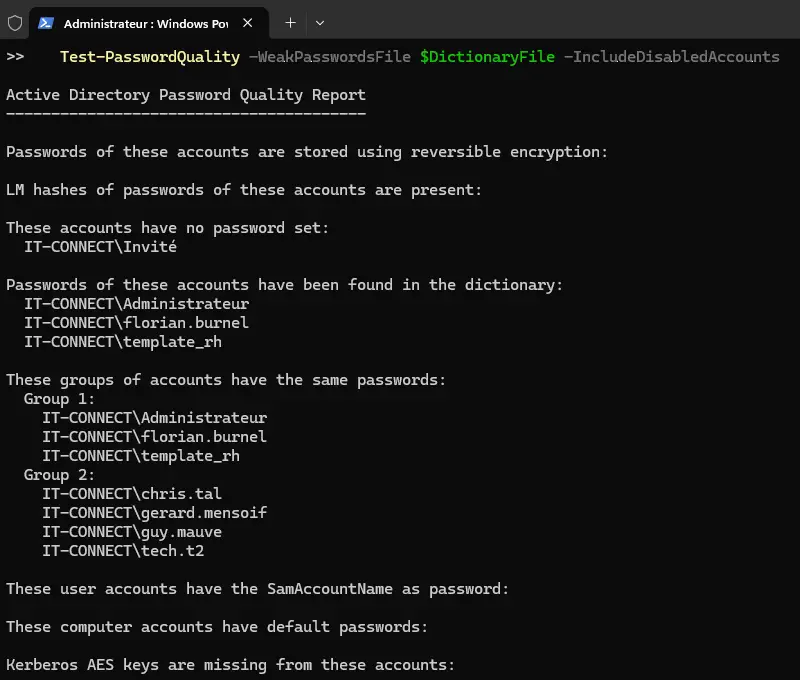
We can see that our dictionary contains the passwords for three accounts:
IT-CONNECT\Administrateur
IT-CONNECT\florian.burnel
IT-CONNECT\template_rhIn addition, two user groups have the same password:
Group 1:
IT-CONNECT\Administrateur
IT-CONNECT\florian.burnel
IT-CONNECT\template_rh
Group 2:
IT-CONNECT\chris.tal
IT-CONNECT\gerard.mensoif
IT-CONNECT\guy.mauve
IT-CONNECT\tech.t2You can run the same analysis without a password dictionary: all tests will be performed, except for the password search.
Note: Passwords cannot be recovered in clear text directly (unless they are defined with reversible encryption), but by comparing hashes we can identify some of them via a dictionary. This is possible because there is no salting for password encryption.
IV. PassTester
Published in 2024, the PassTester tool, written entirely in PowerShell, is used to identify the AD user accounts most vulnerable to a brute force attack (or dictionary attack in general). To perform this analysis, the tool relies on the API of the I Have Been Pwned service to identify compromised passwords.
To avoid exposing your users' password hashes, PassTester performs a query based on the first 5 characters of the password hash. Based on this initial match, the tool retrieves a list of hashes that have these 5 characters in common, and compares them locally with the AD hash. If there is a match, the password can be considered compromised.
You can download the script PassTester.ps1 from the project's official GitHub. You need a domain Administrator account to run the analysis, as the tool works on a database dump. ntds.dit. The advantage is that it can be exported to an infrastructure and then analyzed on another machine disconnected from the customer's IS (if the tool is used as part of a service).
First, run the script and select the option 1 to export the AD database.
.\PassTester.ps1
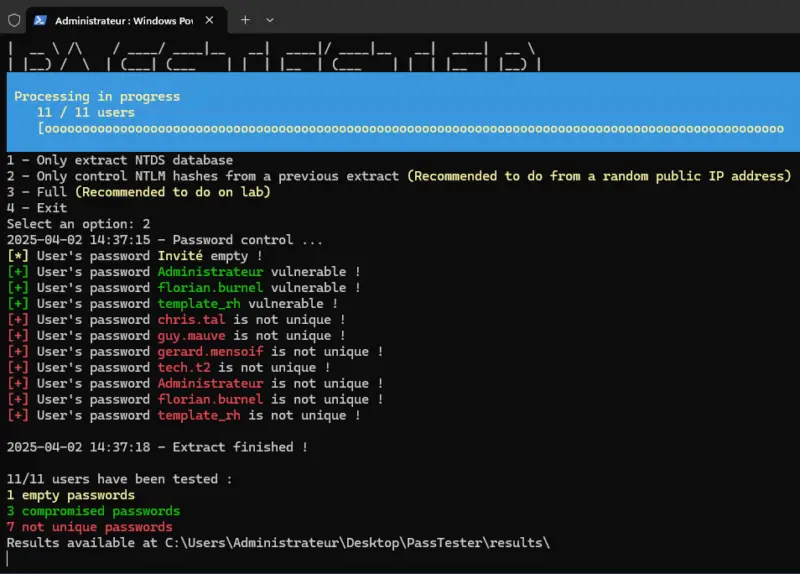
Then rerun the script to select the option 2. This time, the tool will use the export previously carried out, which it retrieves from the desktop of the user at the origin of the execution, to analyze passwords.
.\PassTester.ps1Console feedback indicates, for each user, whether the password is vulnerable or not. What's more, if several users have the same password, the information is also returned, without there being a group as with DSInternals. Here, we can see that 3 users have a vulnerable password.
V. Lithnet Password Protection for AD
The free Lithnet Password Protection for AD solution integrates a number of features, not limited to password auditing. For example, you can use it to block certain passwords (thanks to a customized dictionary).
Like PassTester, the Lithnet tool compares password hashes with the I Have Been Pwn database, with the difference that this tool downloads the database locally. This step is a bit time-consuming: despite a good Internet connection, it took me almost 2 hours to download the data.
You can download the tool here:
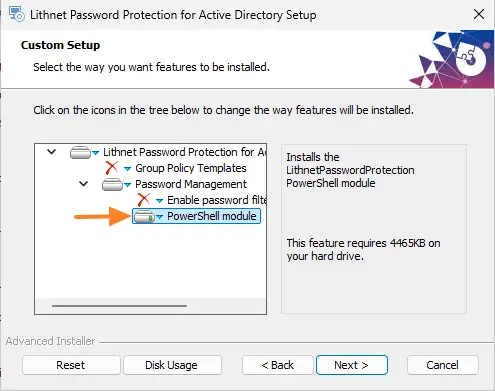
To audit passwords only, install only the "PowerShell module" during installation. Like this:
Next, you need to create a store to host the HIBP password database. This can be a local directory or a shared directory synchronized between several servers using DFS-R.
From a PowerShell console running as administrator, you can create the store as follows:
New-Item -Path "C:\LithnetStore" -ItemType Directory
Import-Module LithnetPasswordProtection
Set-PasswordFilterConfig -StorePath "C:\LithnetStore"Here, we create the blind in the following location: C:LithnetStore. When this is done, open the store via PowerShell :
Open-Store -Path "C:\LithnetStore"Then start password hash synchronization. Wait.... A long pause is in order. There's about 17 GB of data to download.
Sync-HashesFromHibpWhen the operation is complete, there will be an output like this:
OperationStart : 02/04/2025 15:23:10
OperationFinish : 02/04/2025 17:14:36
Duration : 01:51:26.7203447
PagesRetrieved : 1048576
PagesWithChanges : 1048576
PagesUnchanged : 0
NewHashesImported : 1286782039
ExistingHashesDiscarded : 0
TotalHashesProcessed : 1286782039Then you can use the script below, taken from Lithnet's documentation, to analyze your AD. It is based on the Test-IsADUserPasswordCompromised module LithnetPasswordProtection. An output file with the users whose passwords have been compromised will be generated here : C:TEMPget-pwned-users.csv.
Import-Module LithnetPasswordProtection
$file = "C:\TEMP\get-pwned-users.csv"
"accountName,UPN,pwdLastSet,lastLogin,accountDisabled" | out-file $file
$Searcher = New-Object System.DirectoryServices.DirectorySearcher
$Searcher.PageSize = 200
$Searcher.SearchScope = "subtree"
$Searcher.Filter = "(&(objectCategory=person)(objectClass=user))"
$Attributes = @("PwdLastSet","lastLogonTimeStamp", "userAccountControl", "userPrincipalName", "name")
ForEach($Attribute In $Attributes)
{
$Searcher.PropertiesToLoad.Add($Attribute) > $Null
}
$Results = $null
$Total = 0
$NumChanged = 0
$Searcher.FindAll() | % {
$user = $_.Properties["UserPrincipalName"][0]
if ($user -eq $null)
{
write-warning "User $($_.Properties["Name"][0]) has a null UPN";
return;
}
$result = Test-IsADUserPasswordCompromised -UPN $user -server localhost
$pwdLastSet = $null
$lastLogin = $null
$disabled = $false;
if ($_.Properties["PwdLastSet"][0] -gt 0)
{
$pwdLastSet = [DateTime]::FromFileTimeUtc($_.Properties["pwdLastSet"][0]).ToLocalTime()
}
if ($_.Properties["lastLogonTimeStamp"][0] -gt 0)
{
$lastLogin = [DateTime]::FromFileTimeUtc($_.Properties["lastLogonTimeStamp"][0]).ToLocalTime()
}
if (($_.Properties["userAccountControl"][0] -band 2) -eq 2)
{
$disabled = $true;
}
if ($result -ne $true)
{
return;
}
$message = "$($_.Properties["Name"][0]),$user,$pwdLastSet,$lastLogin,$disabled"
Write-Output $message
$message | out-file $file -Append
} The output CSV file contains several pieces of information: account name, UserPrincipalName (UPN), date password last changed, date last logged in, whether the account has been deactivated (true or false). Here's an example:
accountName,UPN,pwdLastSet,lastLogin,accountDisabled
Florian Burnel,florian.burnel@it-connect.tech,09/16/2024 18:43:59,11/29/2024 13:51:38,FalseThe advantage of Lithnet is that all processing is carried out locally. This analysis, which can be integrated into PowerShell scripts, can be automated and run on a regular basis, which is an advantage. On the other hand, this solution focuses solely on the detection of compromised passwords, whereas the other tools mentioned carry out a broader analysis of password-related issues.
VI. Conclusion
There are other free tools for auditing Active Directory passwords, but these 4 already cover the subject very well. More or less lightweight, and more or less complete, they will meet different needs, between those who want a lightweight script, or a complete solution capable of generating a report. It's up to you to choose the tool that most closely matches your requirements.
If you're looking for a simple tool that requires no special technical skills, take a look at Specops Password Auditor. It's the most accessible tool in this selection, and what's more, it's also the only one to generate a report in PDF format.
 www.it-connect.fr
www.it-connect.fr









